The Algorithmic Oracle
From Cold War Forecasting to modern mind control- exposing the Global Infrastructure of Manufactured Concensus
TL;DR: How Your Opinion Is Being Manufactured (And You Likely Don't Even Know It)
The Hidden Weapon Shaping What You Think
Ever wonder why "expert consensus" always seems to emerge on controversial topics? There's a 70-year-old technique called the Delphi method that was originally created by military researchers to predict the future—but it's now being used as a sophisticated weapon to manufacture fake agreement and control what you believe.
What Is the Delphi Method? (The Basics)
Think of it as a rigged survey system:
Step 1: Carefully select "experts" (but you don't know who they are or their biases)
Step 2: Ask them questions anonymously across multiple rounds
Step 3: Show each round's results to influence the next round
Step 4: Keep going until everyone "agrees"
Step 5: Present this manufactured consensus as scientific truth
The problem? The people running it control who counts as an "expert" and what information gets shared between rounds. It's like a magic trick where the outcome is predetermined.
How It Became a Weapon
From Forecasting Tool to Mind Control
What started as a way to predict technology in the 1950s has evolved into something far more sinister. Today's version uses:
Algorithmic feedback loops: Social media algorithms that show you information designed to make you think there's consensus when there isn't
Fake expert networks: Coordinated groups that appear independent but all push the same narrative
Psychological warfare: Exploiting your natural tendency to follow what seems like expert agreement
The Digital Acceleration
Your social media feeds are essentially automated Delphi panels, constantly showing you "evidence" that reinforces predetermined conclusions while making you think you're seeing organic consensus.
The Epistemological War (Why Your Reality Is Under Attack)
Reactionary Epistemology: The Backlash
As people lost trust in institutions, they turned to "bootstrap epistemology"—the idea of justifying one's beliefs or knowledge about a belief-forming process (like perception or memory) by relying solely on that process itself, without external validation often translated as—doing their own research instead of trusting experts. But this created new vulnerabilities because:
You reject institutional gatekeepers but lack resources to verify complex claims
Sophisticated disinformation campaigns can exploit your desire for independent research
You become susceptible to coordinated alternative narratives designed to feel like personal discovery
Who's Using This Against You
The method has been adopted by virtually every major institution:
International: WHO, UN, European Union
Government: U.S. federal agencies, state governments, military
Academic: Universities, research institutions
Medical: Professional societies, public health agencies
Corporate: Technology companies, industry groups
This creates a massive infrastructure where manufactured consensus can be reinforced through multiple "independent" sources simultaneously.
Current Warfare Against America
These operations have intensified dramatically. Foreign and domestic actors are using these techniques to:
Fragment American reality into irreconcilable tribal narratives
Erode trust in all institutions (both good and bad ones)
Create epistemological collapse where shared truth becomes impossible
Paralyze America's ability to recognize and respond to real threats
The Cybernetic Trap
Modern algorithms create self-reinforcing cycles:
You interact with content that confirms your beliefs
The algorithm learns and shows you more of the same creating echo chambers and reinforcing cognitive bias
This creates the illusion that your beliefs represent consensus
You become more confident in positions that may be completely manufactured
The cycle accelerates, creating stronger manipulation over time
Why This Matters Right Now
Your opinions may not be your own: What feels like personal research and rational thinking might be the result of sophisticated manipulation
Consensus isn't consensus: When you see "expert agreement," ask who selected the experts and controlled the process
Both sides are manipulated: The goal isn't to promote specific views but to control the entire spectrum of acceptable debate
Reality is under attack: The ultimate goal is to make shared truth impossible, paralyzing democratic society and intrinsically at odds with the tenets and function of the constitutional republic of the United States.
The Path Forward
Neither blind trust in institutions nor complete rejection of expertise works. Instead:
Recognize the mechanisms: Understanding how consensus is manufactured is the first step in resisting it
Build resilient knowledge communities: Combine institutional resources with grassroots verification
Develop new verification systems: Create ways to evaluate claims that don't depend on potentially captured expert networks
Reclaim cognitive liberty & sovereignty: Protect your ability to think independently while benefiting from collective knowledge
Bottom Line
The Delphi method reveals how your reality is being systematically constructed by others who benefit from your agreement. In an age of algorithmic manipulation and information warfare, understanding these mechanisms isn't academic—it's cognitive self-defense. The battle for your mind is real, sophisticated, and happening right now.
The question isn't whether you're being manipulated. The question is whether you'll recognize it in time to fight back.
▹▹Check out my Radio Show covering the Delphi Method:
Introduction: The Hidden Architecture of Manufactured Agreement
In a world increasingly dominated by algorithmic manipulation and carefully constructed narratives, understanding the mechanisms behind consensus formation has never been more critical. As we witness accelerating information warfare targeting the foundations of American society, cognitive liberty and personal sovereignty, the tools and techniques used to shape mass opinion have evolved far beyond what their creators could have imagined. At the heart of these operations lies a methodology that few recognize but everyone experiences: the Delphi method.
Originally developed as a forecasting tool by RAND Corporation researchers in the 1950s, the Delphi method has transformed from a seemingly innocuous consensus-building technique into one of the most powerful weapons in the arsenal of psychological and epistemological warfare. While presented as a scientific approach to capturing expert opinion, its core mechanisms provide a blueprint for manufacturing artificial consensus that serves power rather than truth.
What follows is an examination of how this methodology has been weaponized across psychological, political, dialectical, and epistemological battlefields—creating self-reinforcing systems of knowledge control that operate below our conscious awareness. As algorithmic feedback loops accelerate and amplify these mechanisms, understanding their operation becomes not just an academic exercise but a matter of cognitive self-defense.
The Delphi Method Unmasked: Origins and Core Mechanics
The Delphi method emerged from the shadowy world of Cold War military research, conceived by the RAND Corporation in Santa Monica, California during the 1950s. Named after the ancient Oracle of Delphi—where priestesses would deliver prophecies from Apollo—the modern technique maintained the same essential function: to provide "authoritative" predictions that guide decision-making. But unlike its mystical namesake, this oracle operated through a carefully constructed scientific methodology.
The Delphi Method's Foundation
The Delphi Method was originally developed at RAND Corporation in the early 1950s by researchers including Norman Dalkey, Olaf Helmer, and Nicholas Rescher as a systematic approach to forecasting and expert opinion gathering. The method was initially designed as "a technique to apply expert input in a systematic manner using a series of questionnaires with controlled opinion feedback" under the auspices of the U.S. Air Force. Key features included preservation of anonymity in expert panel responses and iteration of questionnaires to achieve convergence of opinion.
The original RAND applications focused on national defense and long-range forecasting, with the first unclassified use appearing in RAND reports on technological and social developments. The method employed structured communication techniques to achieve convergence of opinion among expert panels through multiple rounds of anonymous feedback.
The method's creators claimed it was designed to "forecast the impact of technology on warfare," establishing its military origins from inception. This point cannot be overstated—the Delphi method was born, not from disinterested academic inquiry, but from the specific need to control uncertainty in military planning. Its creators understood that whoever could most convincingly predict the future could shape preparation for that future, regardless of whether those predictions were accurate—as I often joke—it’s easy to predict the future when you plan it.
The Mechanics of Manufactured Consensus
At its core, the Delphi method consists of several distinct components that work together to create artificial agreement. This structure creates a carefully managed environment where consensus can be manufactured rather than organically discovered. The anonymity prevents powerful personalities from openly dominating, but simultaneously obscures who is shaping the conversation and their potential conflicts of interest. The iterative rounds with controlled feedback create powerful conformity pressures, as outlier opinions are implicitly discouraged.
Perhaps most importantly, the selection of "experts" provides the ultimate control mechanism—who qualifies as an expert becomes the foundational power lever that determines the range of acceptable opinions before the process even begins. This expert selection creates the boundaries of permissible discourse, constructing the Overton window, a form of pre-censorship that most participants never recognize.
Core Methodology and Key Features
Fundamental Principles
The Delphi method is defined as a systematic process that produces forecasts on technological and social developments through iterative rounds of questionnaires to gather experts' opinions and reach group consensus regarding an issue or topic. According to the RAND Corporation, it "entails a group of experts who anonymously reply to questionnaires and subsequently receive feedback in the form of a statistical representation of the 'group response,' after which the process repeats itself". The goal is to reduce the range of responses and arrive at something closer to expert consensus.
Essential Components
The method incorporates several key features that distinguish it from other consensus-building approaches:
Anonymity: Participants respond independently without knowing the identities of other panel members, which helps prevent dominant personalities from influencing the group
Controlled Feedback: Experts receive statistical summaries of group responses after each round, allowing them to reconsider their positions based on collective input
Statistical Group Response: Results are presented quantitatively to show the distribution of expert opinions
Iterative Process: Multiple rounds allow for refinement of opinions and convergence toward consensus
Typical Process Structure
The standard Delphi process follows a systematic approach involving multiple rounds of data collection and analysis:
Round One: Initial questionnaire gathering broad expert opinions on the topic
Round Two: Refined questionnaire based on first round results, with statistical feedback provided to participants
Round Three and Beyond: Additional rounds as needed until consensus is achieved or stability in responses is reached
Consensus is typically defined using predetermined criteria, such as 70-75% agreement among participants, though this threshold can vary depending on the study's requirements.
Types and Variations
Classical vs. Modified Approaches
While the original Delphi method established specific procedural standards, the literature reveals numerous modifications in how the technique is applied. These variations have emerged to address specific research contexts and practical constraints:
Classical Delphi: Follows the original RAND Corporation methodology with strict adherence to anonymity, multiple rounds, and statistical feedback.
Modified Delphi: Incorporates adaptations such as:
Changes in delivery mode (online vs. paper-based surveys)
Variations in the number of rounds
Different consensus criteria
Real-time or face-to-face meetings combined with anonymous surveys
Inclusion of reference groups or steering committees
Specialized Applications
The method has been adapted for various specific purposes, including policy Delphi for decision-making, numerical Delphi for quantitative forecasting, and historical Delphi for retrospective analysis. These variations demonstrate the flexibility and adaptability of the core methodology to different research contexts and objectives.
Organizations That Have Adopted the Delphi Method for Policy Development
Since the RAND Corporation's initial development of the Delphi method in the 1950s, numerous organizations across multiple sectors have adopted this structured consensus-building methodology to develop local and national policies.
The Institutional Infrastructure: Mapping the Consensus Manufacturing Empire
The theoretical framework for understanding how the Delphi method has been weaponized in epistemological warfare. The scope of organizational adoption reveals not just widespread use, but a systematic pattern of institutional capture that spans every level of governance and authority, that has made this transformation possible..
The interconnected nature of these warfare domains creates self-reinforcing systems that operate across institutional boundaries, making detection and resistance increasingly difficult for those outside the expert networks. Understanding which organizations have adopted these techniques becomes crucial for recognizing how seemingly independent sources can coordinate to manufacture consensus.
The Evolution from Scientific Tool to Warfare Apparatus
The transformation of the Delphi method from legitimate research tool to consensus manipulation apparatus follows a clear historical progression that demonstrates increasing sophistication and reach.

This timeline reveals how James Ferrier's original epistemological framework laid the groundwork for systematic knowledge control, which RAND Corporation then operationalized through the Delphi method, ultimately culminating in today's algorithmic warfare systems. (well go into more detail on this later in this essay). Each phase built upon previous developments while expanding the scope and reducing the visibility of manipulation mechanisms.
Van Harvey and I discuss James Ferrier and the origins of epistemology in this episode:
The Cybernetic Control Architecture
The modern weaponization of the Delphi method operates through sophisticated cybernetic feedback loops that create self-reinforcing systems of consensus manipulation. These systems transform the original method's components into interconnected control mechanisms.
This cybernetic architecture demonstrates how expert selection, controlled feedback, manufactured consensus, authority validation, and information dissemination create circular systems that strengthen manipulation over time. The feedback loops ensure that each component reinforces the others, creating increasingly sophisticated control mechanisms.
The comprehensive organizational landscape revealed in this analysis demonstrates how the Delphi method has been systematically deployed across every sector of society. From international organizations like the WHO and UN system to national governments, academic institutions, and industry groups, the method has created a vast infrastructure for manufacturing consensus.
Quantifying the Institutional Reach
The scope of organizational adoption becomes clear when we examine the distribution across different sectors and levels of governance.
This distribution reveals how national government agencies represent the largest category of adopters, followed by healthcare organizations and international bodies. The widespread adoption across diverse organizational types creates multiple pathways for consensus manipulation that operate simultaneously. Each category serves different functions within the broader epistemological warfare apparatus.
The Global Consensus Machine: International Organizations
The World Health Organization represents perhaps the most sophisticated example of institutional Delphi method deployment, utilizing the methodology across various policy domains while employing expert networks from 40 countries across all six WHO regions. The organization has employed this methodology for developing international consensus on medical standards, including expert consensus on minimum and optimal psychiatric bed numbers. Additionally, WHO has used Delphi methods in conjunction with its Handbook for Guideline Development to establish clinical practice guidelines, such as those for robotic surgical procedures.
The organization has also applied the Delphi method to develop diagnostic criteria and nomenclature standards, including international expert consensus studies for conditions like gaming disorder in the ICD-11 classification system. WHO's approach often involves multiple rounds of expert consultation to reach consensus on complex health policy issues.
Their approach demonstrates how the method's expert selection mechanisms create global authority structures that appear scientific while serving predetermined policy objectives.
Healthcare and Medical Organizations
Medical Professional Societies
Numerous medical professional societies have adopted Delphi methodology for developing clinical guidelines and policy standards . The Japanese Society for Palliative Medicine used modified Delphi methods involving 20 expert panelists to develop Japan's first national consensus syllabus for palliative medicine physicians .
International medical organizations have employed Delphi techniques for establishing diagnostic criteria and treatment guidelines. Medical societies have used the method to reach consensus on complex clinical issues where empirical evidence may be limited, such as developing criteria for sperm DNA fragmentation testing involving 436 experts from 55 countries.
Public Health Agencies
Public health agencies at various levels have incorporated Delphi methodology into their policy development processes . These organizations have found the method particularly valuable for developing guidelines in emerging health areas where traditional evidence may be insufficient.
The method has been especially useful for developing policies related to global health initiatives, where they are seeking coordination among diverse stakeholders across different countries and organizations.
United Nations System
Various UN agencies have incorporated Delphi methodology into their policy development processes. The method has been particularly valuable for addressing global challenges where expert consensus is needed across diverse stakeholder groups. UN system organizations have used modified Delphi approaches to identify strategic priorities for global initiatives, such as drowning prevention strategies that involved 134 participants from research, policy, technical, and community backgrounds across multiple countries.
The United Nations system has incorporated these techniques for strategic priority identification, using modified approaches that create the appearance of global grassroots consensus while operating through carefully controlled expert networks.
European Union
The European Union has adopted Delphi methodology for various policy development initiatives across member states. The European Union's adoption enables supranational governance by manufacturing consensus that overrides national sovereignty, creating artificial agreement that justifies centralized control.
Here’s an example of the Delphi Method being used to plan the future policy for the Taxation and Customs Union:
European National Governments
Finland's government has applied Delphi methodology for agricultural policy development in the context of European Union Common Agriculture Policy implementation. The Finnish approach involved extensive farmer consultation through aggregative Delphi methods to understand stakeholder perspectives on future agricultural directions.
Various European national governments have used Delphi techniques for drug policy evaluation and foresight studies. Finland conducted comprehensive Delphi panel studies between 2009-2011 to assess drug-related policy predictions and their accuracy over a ten-year period.
Domestic Consensus Engineering: National Government Adoption
United States Federal Agencies
Multiple U.S. federal agencies have incorporated Delphi methodology into their policy development processes. Here’s an example from transportation.gov. The approach has been used across various departments for developing evidence-based policies in complex technical domains. Federal agencies have found the method particularly valuable for coordinating multi-agency initiatives, such as the Interagency Collaboration for Genomics for Food and Feed Safety, which involves agencies including the CDC, FDA, USDA, and NIH.
This federal adoption reveals how the technique enables bureaucratic coordination that bypasses democratic oversight.
Asian Government Agencies
Several Asian governments have similarly embraced Delphi methodology for national policy development. Taiwan's Ministry of Economic Affairs (MOEA) used the Delphi method for policy evaluation of programs encouraging multinational corporations to establish R&D centers in Taiwan. The ministry conducted two rounds of Delphi surveys to gather expert suggestions and evaluate the policy's effectiveness in building research networks between local and international organizations.
South Korea has employed Delphi methodology for healthcare policy development, with government agencies using the method to establish priority tasks for building sustainable healthcare systems. The Korean approach involved healthcare professionals in identifying critical policy areas including National Health Insurance reform and public health crisis response strategies.
Japan's government agencies have utilized modified Delphi methods for developing national medical education standards, working with professional medical societies to establish consensus syllabi for palliative medicine. This approach involved coordination between government policy makers and medical professional organizations.
This medical adoption demonstrates how the technique enables the medicalization of behavior through manufactured expert agreement.
Academic and Corporate Capture
Academic institutions have adopted Delphi methodology for research and policy development purposes, using the method to develop institutional policies related to research priorities and evaluation frameworks. This academic adoption enables intellectual capture by creating the appearance of scholarly consensus while serving funding and institutional interests.
Industry organizations have employed the technique for developing sector-specific policies and standards, with the technology sector using Delphi methods to establish competency models, and the construction industry employing them for digital transformation frameworks. The technology sector has used Delphi methods to establish competency models and technical requirements, such as developing 5G competency frameworks with 46 elements across three categories. Professional organizations in industries such as construction have employed Delphi techniques to assess digital transformation readiness and develop implementation frameworks.
Defense and Military Organizations
Military organizations have utilized Delphi methodology for policy development and strategic planning. For instance the Royal Malaysian Air Force employed Fuzzy Delphi Methods to determine optimal maintenance strategies, demonstrating the application of Delphi techniques in defense policy contexts. Defense and military organizations have utilized the methodology for policy development and strategic planning, demonstrating the application in contexts where the method's original military origins become explicit.
Local and Regional Implementation
State and regional governments have adopted Delphi methodology for various policy development initiatives, often focusing on sector-specific policies such as tourism development where expert panels forecast industry trends and develop strategic policies. Municipal and local authorities have used the methodology for community-based policy development, demonstrating the scalability from international to local contexts.
This creates nested systems of consensus manipulation that operate at every level of governance, from international organizations down to municipal authorities. The comprehensive adoption ensures that manufactured consensus can be reinforced through multiple institutional channels simultaneously.
Specialized Domain Control
Environmental and climate policy organizations have adopted Delphi methodology for developing consensus on complex ecological issues, with the method proving particularly valuable for policies related to circular economy implementation where manufactured scientific consensus can justify massive economic transformation. Emergency management organizations have incorporated these techniques for building consensus among diverse stakeholders in crisis management contexts.
The Pattern of Systematic Weaponization
The widespread adoption across these diverse organizational contexts reveals a systematic pattern of institutional capture that transforms legitimate consensus-building into comprehensive infrastructure for manufacturing agreement that serves power rather than truth. Each institutional application creates precedent and legitimacy for expanded use, while the method's anonymous expert selection mechanisms obscure the interests being served.
The transformation from legitimate research tool to consensus manipulation apparatus demonstrates how seemingly neutral methodologies can be systematically weaponized through institutional adoption. The extensive organizational infrastructure now employing these techniques creates a self-reinforcing system where manufactured consensus appears legitimate because it emerges from apparently independent expert sources across multiple institutions.
Understanding this institutional landscape becomes crucial for recognizing how epistemological warfare can operate through established channels rather than obvious propaganda. The legitimate façade of scientific methodology combined with institutional authority creates perfect cover for systematic consensus manipulation that shapes policy outcomes while maintaining plausible deniability.
This comprehensive mapping of institutional adoption reveals the true scope of the challenge we face in defending against epistemological warfare. When hundreds of organizations across every sector of society have adopted techniques that can be weaponized for consensus manipulation, the task of maintaining authentic self-governing discourse becomes exponentially more difficult. Recognition of this infrastructure represents the first step in developing effective countermeasures against the systematic manufacturing of consensus in the service of power.
The Weaponization: From Forecasting Tool to Warfare Technique
What began as a method for technological forecasting rapidly evolved into something far more insidious. As organizations recognized the power of the technique's core mechanisms—anonymous authority, controlled feedback, and manufactured consensus—they began applying it across increasingly diverse domains. The transition from forecasting to warfare came through the realization that consensus itself could be weaponized.
This article by Gerald L. Atkinson, argues, “the Delphi Technique is a deceptive, manipulative and unethical group dynamics method which exploits human social instincts in order to coerce people into a preordained group ‘consensus.’”
to learn more about “group dynamics” see my episode on sensitivity training here:
The evolution followed a predictable path: from military applications to government policy development, then to corporate strategy, and finally to mass opinion formation. At each stage, the method became more sophisticated while its fundamental mechanisms remained constant. The controlled environment of the original method expanded to encompass the entire information ecosystem.
The Connection Between the Delphi Method and Sensitivity Training: Shared Origins in Psychological Group Control
The Delphi Method and sensitivity training share fundamental connections rooted in post-World War II psychological research, both emerging from efforts to understand and manipulate group behavior for predetermined outcomes. These methodologies represent parallel developments in what can be characterized as systematic approaches to consensus building and behavior modification through controlled group dynamics.
Historical Origins and Institutional Connections
The Tavistock-RAND Nexus
The connection between the Delphi Method and sensitivity training can be traced to their shared institutional and intellectual heritage. The Delphi Technique was developed by RAND Corporation in the late 1950s, initially as a method for forecasting trends to help managers make production decisions. However, according to documented sources such as Stuart Chase, The Proper Study of a Mankind, it evolved into "a process of separating supporters from detractors in small-group situations so that a predetermined consensus could be manipulated by the 'facilitator'".
John Rawlings Rees and Psychological Control Methods
The connection between the Delphi Method and sensitivity training becomes apparent through the work of the Tavistock Institute under John Rawlings Rees. Rees, who headed the Tavistock Clinic beginning in 1932, developed what became known as the "Tavistock Method" of mass psychological control involving, what Eakman referred to as "the deliberate inducement of neurosis"; suggesting this approach aimed to create psychologically controlled environments for manipulating populations through mass media and group dynamics.
The Tavistock Institute initiated sensitivity training techniques in the United Kingdom and collaborated with American behavioral scientists to refine these methods. The institute conducted tests on American and British soldiers to determine “whether under conditions of induced and controlled stress, groups could be made to behave erratically” and whether people would abandon firmly held beliefs under peer pressure.
“Sensitivity training is based on research on human behavior that came out of efforts during World War II to ascertain whether or not an enemy’s core beliefs and behavior could be modified by the application of certain psychological techniques. These techniques have been gradually perfected over the years by efforts of business and industry leaders to persuade people to buy products, including the radio and television industry to ascertain how an audience might be habituated to certain types of programming.”
The CIA released statements from 1974 questioning the use of “sensitivity training”. They indicated that the group dynamics could destroy objective individual judgement, as evinced in China’s brainwashing program.
Evolution into the Delphi Technique
The process of evolving the Tavistock Method, involves creating controlled stress situations by group leaders with predetermined goals, using peer pressure in gradually increasing increments to intimidate weaker individuals into conforming. The method was refined and popularized by various schools of behavioral science, including the Esalen Institute and Western Training Laboratories in Group Development .
Kurt Lewin's Foundational Influence
Both methodologies trace their theoretical foundations to Kurt Lewin's work in group dynamics and behavior modification. Lewin, described as "the father of sensitivity training in the United States," was instrumental in developing systematic approaches to changing individual and group behavior. His work at MIT and the National Training Laboratory (NTL) in Bethel, Maine, established the theoretical framework that would influence both sensitivity training and consensus-building techniques. Kurt Lewin founded the Research Center for Group Dynamics at the Massachusetts Institute of Technology (MIT) in 1945, where he served as its director until his death in 1947. His research led to the development of the T-group (training group) methodology, which became influential in organizational psychology and group therapy.
Lewin contributed to the Office of Strategic Services (OSS), the precursor to the CIA, by applying his expertise in group dynamics to the training of spies and saboteurs. The OSS, tasked with intelligence and covert operations, utilized Lewin's T-group model to develop leadership and team-building skills for operatives who were parachuted into occupied territories to gather intelligence and support allied efforts. His contributions to the OSS were part of a larger collaboration with psychologists and researchers who applied social science to national security efforts.
Lewin’s academic career began at the University of Berlin, where he was exposed to Wundtian psychology but gravitated toward Gestalt psychology and social psychological problems. His work emphasized the interplay between individuals and their environments, encapsulated in his famous equation, B = f(P, E), where behavior is a function of the person and their environment. After immigrating to the United States in 1933 due to Nazi persecution, Lewin continued to influence social psychology through institutions like MIT, Cornell and the University of Iowa.
I discuss Wilhelm Wundt in these two episodes:
Kurt Lewin was "an important influence on the work of the Tavistock" according to Eric Trist, and his group dynamics theory became foundational to understanding how groups could be manipulated. Lewin's three-stage change process of "unfreezing, transitioning, and refreezing" became the template for systematic organizational transformation.
Kurt Lewin and the Birth of Change Agency
The modern concept of change agents traces directly to Kurt Lewin (1890-1947), widely recognized as the founding father of organizational development and applied behavioral science. Lewin, a Polish-born, German-educated social psychologist who fled Nazi Germany for the United States in 1933, established the theoretical and practical foundations that continue to underpin change agent methodology today. His work at MIT and later institutions introduced fundamental concepts including action research, group dynamics, and force field analysis that became essential tools for change agents.
Change agents represent individuals who actively facilitate transformation within organizations and social systems through systematic approaches to planned change. The concept emerged from foundational work in social psychology and organizational development, evolving into a comprehensive framework for understanding how individuals can effectively drive institutional and cultural transformation. At its core, a change agent serves as a catalyst who uses specific methodologies, interpersonal skills, and strategic approaches to overcome resistance and implement sustainable improvements.
Lewin's approach was grounded in the belief that "there is nothing so practical as a good theory," emphasizing the importance of rigorous research methods combined with real-world application. His three-stage change process of unfreezing, transitioning, and refreezing became the template for systematic organizational transformation. During World War II, Lewin experimented with collaborative change processes involving himself as consultant and client groups, establishing the foundation for what would become action research methodology.
The National Training Laboratory and Institutionalization
Following Lewin's unexpected death in 1947, his colleagues Leland Bradford, Kenneth Benne, and Ronald Lippitt established the National Training Laboratory (NTL) in Bethel, Maine, fulfilling Lewin's vision of creating a systematic approach to training change agents. The NTL became the epicenter for developing what would be called "change agents" - individuals specifically trained to facilitate organizational and social transformation. Located in the remote mountains of Maine, Bethel was chosen because Lewin believed that "change could more readily occur if the learning happened some distance from the participant's home environment".
The NTL's mission centered on training and developing change agents through innovative methodologies including T-groups, experiential learning, sensitivity training, and feedback methods. These approaches influenced social institutions, industry, and organizations worldwide, establishing the foundational practices that continue to define change agent work today. The Institute's work linked teacher training with classroom teaching and extended into multiple domains beyond education.
Core Methodologies and Recruitment Approaches
Action Research and Group Dynamics
Change agents employ action research as their primary methodology - a participatory problem-solving approach where groups collaboratively analyze, address, and resolve organizational challenges. This cyclical process involves diagnosis, analysis, feedback, action, and evaluation, creating a systematic framework for implementing and assessing change initiatives. Action research enables change agents to gather direct input from stakeholders, establishing new business processes while continuously monitoring outcomes through ongoing improvement cycles.
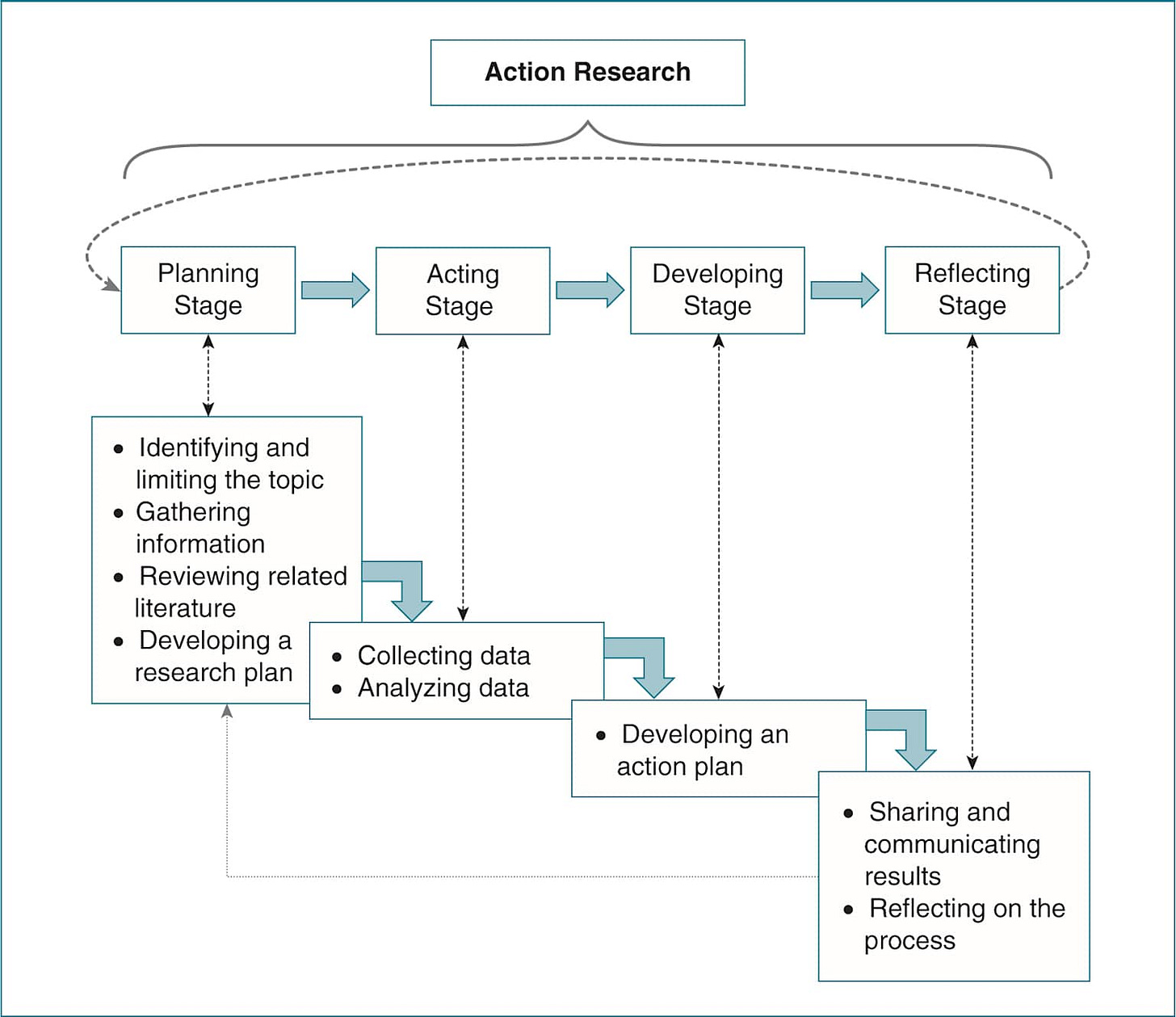
Group dynamics theory, another cornerstone of change agent methodology, examines how groups behave and interact within organizational contexts. This psychological approach helps change agents understand employee reactions to change, enabling them to address resistance and remove barriers to transformation. Force field analysis complements these approaches by examining factors that either hinder or enable movement toward organizational goals.

Sensitivity Training and T-Groups
Sensitivity training, implemented through T-groups (training groups), represents one of the most significant innovations in change agent development. These small group sessions focus on interpersonal dynamics, feedback, and personal awareness, helping participants understand their impact on others and develop more effective leadership capabilities. T-groups became a standard component of change agent training, providing experiential learning opportunities that could not be replicated through traditional educational methods.

The methodology spread rapidly from its origins at NTL to corporate training programs throughout the 1950s and 1960s. Organizations recognized that systematic approaches to group development and interpersonal skills training could significantly enhance their change management capabilities. The influence of T-groups extended beyond corporate settings into education, social work, and community development.
Tavistock’s Leicester Conference has been offering change agent training since 1957:
Relationship to the Delphi Method
While the Delphi Method emerged independently from change agent theory, it shares important connections through its focus on systematic consensus-building and expert consultation processes. Developed at RAND Corporation in the 1950s, the Delphi Method uses structured communication techniques to achieve convergence of opinion among expert panels. Change agents often incorporate Delphi techniques when implementing large-scale organizational transformations that require input from multiple stakeholders across different levels and functions.
The methodology proves particularly valuable for change agents working on complex initiatives where traditional group meetings might be impractical or where anonymous input helps overcome hierarchical barriers. Both approaches emphasize iterative processes, systematic data collection, and collaborative decision-making, making them complementary tools for comprehensive change initiatives.
Applications Across Domains
Educational Reform
“Charlotte Iserbyt argues that since the 1960s the American education system has undergone dramatic changes, i.e. from traditional education whcih aimed at academic skills, individual faculties and high literacy to a school-to-work traing, also know by synonyms such as workforce training, outcome-based education (OBE), mastery learning or direct instruction. The new system, she argues, is strongly based on skinner's 'stimulus-response-stimulus operant conditioning' philosophy, which compares human beings with animals who also learn by a positive response strategy. Skinner, however, forgets that human beings are also equipped with consciousness, conscience and emotions and aer not robot-like beings. During the past decades the new approach to education (i.e. training) has been disseminated by so-called 'change agents' across all the US. These agents were self-proclaimed proponents (mostly university professors and politicians) who turned to teachers and local schoolboard members in order to propagate their ideas. By lowering standards through standardized tests which are mostly based on multiple choice and false/right answers, they are trying to train people for the economy and industry. Job placements and community or social work are parts of the new curriculum. Teaching in front of the classrom by discussing human issues or literature was substituted by prescribed teaching modules and narrow-scaled competencies.”
I highly recommend Charlotte’s book, “The Deliberate Dumbing Down of America”.
In educational settings, change agents focus on curriculum reform, instructional improvement, and systemic transformation of learning environments. Teacher change agents work within schools and districts to implement evidence-based practices, promote diversity and inclusion initiatives, and drive adoption of innovative pedagogical approaches. These educators use action research methodologies to identify problems, develop solutions, and assess the effectiveness of interventions.
Educational change agents operate at multiple levels, from individual classrooms to entire school systems. They serve as facilitators who help colleagues examine their practice, analyze student data. The role of change agents have become increasingly important as schools face pressure to address achievement gaps, integrate technology, and respond to changing student demographics.
Military Organizational Transformation
Military organizations employ change agents to drive cultural transformation, improve operational effectiveness, and implement new doctrines or technologies. These initiatives often focus on leadership development, values integration, and behavioral change programs designed to enhance unit cohesion and performance. Military change agents work to overcome institutional inertia and traditional resistance to new approaches.
The military's hierarchical structure presents unique challenges and opportunities for change agents. While formal authority can accelerate implementation, sustainable change requires buy-in from personnel at all levels. Military change agents often focus on embedding new practices into training programs, standard operating procedures, and performance evaluation systems.
Cultural and Social Movements
Change agents in cultural and social contexts work to promote social justice, environmental awareness, and community development. These individuals often operate outside formal organizational structures, using grassroots organizing, advocacy, and coalition-building to drive systemic change. Their methods include community education, protest organization, policy advocacy, and cultural programming designed to shift public attitudes and behaviors.
Social movement change agents rely heavily on networks, media engagement, and strategic partnerships to amplify their influence and achieve their objectives.
Political Advocacy and Policy Change
Political change agents work within and outside government structures to influence policy development, electoral outcomes, and institutional reforms. These individuals employ lobbying, grassroots organizing, coalition building, and public education campaigns to advance their agendas. They often serve as intermediaries between citizen groups and policymakers.
The CIA's MICE to RASCALS Framework
The Central Intelligence Agency's 2013 document "An Alternative Framework for Agent Recruitment: From MICE to RASCALS" by Randy Burkett represents a significant evolution in understanding change agent recruitment and motivation. This document directly addresses limitations in the traditional MICE framework (Money, Ideology, Coercion/Compromise, Ego/Excitement) used for recruiting intelligence assets and proposes the RASCALS model based on Robert Cialdini's principles of influence.
The RASCALS framework consists of six influence factors: Reciprocation, Authority, Scarcity, Commitment/Consistency, Liking, and Social Proof. Burkett argues that these psychological principles provide a more sophisticated understanding of human motivation than the MICE framework, which he considers outdated for contemporary recruitment challenges. The document demonstrates how intelligence agencies have adopted change agent methodologies originally developed for organizational development.
This evolution illustrates the broad applicability of change agent concepts across domains, from corporate training programs to intelligence operations. The RASCALS framework reflects modern understanding of influence and persuasion that emerged from the same social psychological traditions that produced organizational development. Intelligence officers trained in these techniques become more effective "compliance specialists" capable of understanding and leveraging complex motivational factors.
Methodological Similarities and Shared Techniques
Consensus Manipulation Through Facilitation
Both the Delphi Method and sensitivity training employ skilled facilitators to guide groups toward predetermined outcomes while maintaining the appearance of democratic participation. In sensitivity training, facilitators use specific psychological techniques to break down individual resistance and create group conformity. Similarly, the Delphi Method employs "controlled opinion feedback" to guide expert panels toward consensus.
The role of the facilitator is central to both methodologies. According to the documented analysis, change agents (facilitators) are trained to serve as "lightning rods” in a small group to draw out the objections (and more important, the objectors) so that the target group can be manipulated toward the predetermined affirmative outcome. This process involves the facilitator acting as an advocate-organizer-agitator who gains trust, identifies resistance, and then systematically eliminates opposition.
Psychological Pressure and Group Conformity
Both techniques exploit psychological mechanisms of group behavior to achieve compliance. Sensitivity training uses "controlled stress situations" created by facilitators with the goal of achieving consensus that has been "predetermined". The method employs "peer pressure in gradually increasing increments, up to and including yelling at, cursing at, and isolating the holdouts" to force weaker individuals to conform.
Research on group dynamics demonstrates that "people in groups tend towards agreement" and "there is always a strain to find which position is correct or appropriate" . This natural tendency toward consensus is exploited by both methodologies to achieve predetermined outcomes.
Iterative Refinement Processes
Both the Delphi Method and sensitivity training employ iterative processes to refine and strengthen consensus. The Delphi Method uses multiple rounds of questionnaires with feedback between rounds, allowing facilitators to guide participants toward the desired outcome. Sensitivity training similarly uses repeated sessions and ongoing group pressure to reinforce behavioral changes.
Modern applications of the Delphi Method continue to emphasize consensus building through structured iteration. Studies demonstrate how "the purpose of the study and the homogeneity of the sample are crucial factors when designing the Delphi procedure".
Applications in Social Control and Behavior Modification
Educational and Organizational Implementation
Both methodologies have been extensively implemented in educational and organizational settings to achieve systematic behavior modification. Sensitivity training has been "successfully employed by behavioral scientists in the service of the Federal Government over the past thirty years to implement radical curriculum changes in K-12 education".
The Alinsky Method, described as "a specialized application of this 'change agent' technique, applied specifically to teachers," became "a staple of the National Education Association (NEA)". Saul Alinsky's approach emphasized that "any revolutionary change must be preceded by a passive, affirmative, non-challenging attitude toward change among the masses of people".
Military and Corporate Applications
Both techniques have been adopted by military and corporate organizations for systematic culture change. Sensitivity training is "being used nationwide to force military personnel, officer and enlisted, to accept the radical notion that women should engage in combat". Similarly, consensus-building techniques derived from the Delphi Method are widely used in corporate settings to implement organizational changes.
Contemporary Manifestations and Ongoing Influence
Modern Consensus Building Techniques
Contemporary consensus-building methodologies continue to employ principles derived from both the Delphi Method and sensitivity training. Modern facilitation techniques include methods such as "Fist to Five" voting, "dot voting," and "confidence voting" that maintain the appearance of democratic participation while guiding groups toward predetermined outcomes.
Professional facilitators are trained in techniques that echo the historical approaches described in the source material. Research demonstrates how "facilitators play in navigating the balance between cohesion and diversity" and how "facilitative actions can successfully enhance group cohesion by mitigating the negative effect of faultiness".
Digital Age Applications
The principles underlying the Delphi Method, Sensitivity Training and the Alinsky Method have been adapted for digital platforms and online consensus building. Modern applications include visual collaboration platforms, and digital tools that naturally record the results of consensus-building activities, while maintaining facilitator control over outcomes.
The connection between the Delphi Method and sensitivity training extends far beyond superficial similarities in group facilitation. Both methodologies emerged from the same post-World War II research environment focused on understanding and controlling group behavior. They share common theoretical foundations in Kurt Lewin's group dynamics work and employ similar psychological techniques to manipulate consensus while maintaining the appearance of unconstrained participation.
Evidence suggests that these techniques represent sophisticated approaches to social control that operate by exploiting natural human tendencies toward group conformity. Their continued influence in educational, military, corporate, and political settings demonstrates the enduring power of these methodologies to shape behavior and opinion on a mass scale. Understanding these connections provides crucial insight into how seemingly neutral facilitation techniques can serve as tools for systematic social engineering and behavior modification.
Psychological Warfare Applications
In psychological warfare operations, the Delphi method's principles enable the construction of artificial authority structures that appear legitimate while serving specific objectives. The technique creates the impression of independent expert agreement on contested issues, manufacturing perceived consensus that can be deployed against target populations.
Military psychological operations have adapted these techniques to create believable narratives that serve strategic objectives rather than truth. By carefully controlling who qualifies as an expert, what feedback participants receive, and how consensus is measured, psychological warfare operators can engineer agreement on virtually any proposition.
This mechanism proves particularly effective because humans are social creatures who naturally defer to perceived expert consensus. When presented with what appears to be unified expert opinion, most people will conform rather than challenge the apparent authority—even when that consensus contradicts their own direct experience.
Examples of Military Psychological Operations: Weaponizing the Delphi Method for Strategic Narrative Creation
Military psychological operations have systematically adapted the Delphi method's consensus-building framework to manufacture expert agreement on strategic narratives that serve policy objectives rather than truth. These operations exploit the method's core vulnerabilities—expert selection, controlled feedback, and consensus measurement—to create artificially manufactured agreement that appears scientifically legitimate while advancing predetermined military and political goals .
The sophistication of these techniques has evolved dramatically since the 1950s, progressing from crude propaganda to sophisticated epistemological warfare that operates below public awareness. Modern applications integrate algorithmic amplification with traditional expert manipulation to create self-reinforcing consensus that becomes increasingly difficult to detect or counter.

Expert Selection Control: Manufacturing Authority Networks
Defense Contractor Academic Funding
One of the most pervasive examples involves defense contractors systematically funding academic positions and research programs to create networks of ostensibly independent experts who consistently support military-industrial complex interests . The RAND Corporation's role in manufacturing expert consensus for the Iraq WMD analysis demonstrates how careful expert selection can produce predetermined conclusions while maintaining scientific credibility .
The RAND Corporation's expert analysis supporting Iraqi WMD claims demonstrates comprehensive Delphi method weaponization. Expert selection privileged intelligence community insiders while excluding skeptical voices, controlled feedback emphasized threat indicators while minimizing contradictory evidence, and consensus measurement focused on agreement thresholds that supported predetermined intervention objectives.
The operation successfully created expert consensus justifying military intervention despite subsequently proven false premises.
Funding relationships create powerful incentives for academic compliance, where career advancement becomes dependent on producing research that aligns with sponsor objectives. Universities receiving substantial defense funding develop institutional pressures that subtly shape research priorities and conclusions, creating the appearance of independent scholarly consensus while serving strategic communication goals .
Security Clearance Gatekeeping
The intelligence community exploits security clearance requirements to create insider-outsider dynamics that privilege cleared experts while marginalizing independent voices. This mechanism was particularly evident in COVID-19 lab leak discussions, where experts with government affiliations were positioned as authoritative while independent researchers raising alternative hypotheses were excluded from policy deliberations .
The clearance system creates a self-reinforcing dynamic where experts must demonstrate ideological reliability to maintain access, gradually filtering out dissenting perspectives and creating homogeneous expert networks that reliably produce consensus supporting official narratives.
Think Tank Placement Networks
Strategic placement of experts within influential think tanks like the Atlantic Council, Brookings Institution, and Center for Strategic and International Studies creates the appearance of diverse institutional support for predetermined positions. These organizations, while maintaining facades of independence, often coordinate messaging through shared funding sources and overlapping personnel networks.
The Syria chemical weapons attribution campaigns exemplify this approach, where experts from multiple think tanks appeared to independently converge on identical conclusions, creating false consensus that influenced international policy decisions.

Feedback Manipulation: Engineering Information Environments
Selective Information Sharing
Operation Mockingbird and its contemporary successors demonstrate how controlling information flow to expert participants can manufacture consensus by ensuring they only encounter evidence supporting predetermined conclusions. Participants in these manipulated consultation processes believe they are making independent judgments while operating within carefully constructed information bubbles.
The COVID-19 pandemic revealed sophisticated information manipulation where scientific experts were provided selective data and faced professional pressure to conform to evolving official narratives. Medical societies published "expert consensus" recommendations that reflected political rather than purely scientific considerations, demonstrating how feedback control can shape professional medical opinion.
Manufactured Urgency and Pressure
Time pressure becomes a powerful tool for preventing thorough analysis and promoting conformity to emerging group positions. The Iraq weapons inspection process exemplifies this technique, where inspectors faced intense pressure to reach rapid conclusions that supported predetermined policy objectives.
Military psychological training programs systematically employ manufactured urgency to override individual critical thinking and promote adherence to group consensus. The SERE program demonstrates how controlled stress environments can be used to study and manipulate expert decision-making processes.
False Consensus Signals
Sophisticated operations create artificial signals of emerging consensus to influence remaining participants toward predetermined positions. Climate science discussions reveal how false consensus signals were systematically deployed to marginalize dissenting views while creating the appearance of overwhelming scientific agreement.
The Club of Rome admitted in their First Global Revolution 1991 document, that they were searching for a “common enemy”. It appears the Delphi Method has been utilized to maintain this lie to serve the advancement of Agenda 21 and the UN sustainable development goals.
These techniques exploit psychological conformity pressures, where individual experts modify their positions based on perceived group opinion rather than independent analysis of evidence.
Consensus Engineering: Predetermined Outcome Manufacturing
Statistical Manipulation and Threshold Adjustment
Intelligence community assessments demonstrate sophisticated statistical manipulation where consensus thresholds could be adjusted to achieve desired outcomes. The presentation of "high confidence" intelligence assessments could easily reflect manipulated consensus rather than genuine expert agreement based on available evidence. 2002 Iraq WMD NIE provides an example of a historical case where consensus processes and confidence levels raised concerns regarding potential manipulation.
Policy research institutes have been suspected to employ similar techniques, adjusting methodological parameters until achieving statistical results that support predetermined policy recommendations. These manipulations maintain scientific legitimacy while serving strategic communication objectives. Systematic exclusion of dissenting experts from subsequent consultation rounds creates artificial consensus by eliminating alternative perspectives.
Congress for Cultural Freedom (1950-1967)
The CIA's Congress for Cultural Freedom represents the most sophisticated historical example of Delphi method weaponization for cultural and ideological influence. The operation systematically controlled expert selection through funding mechanisms, manipulated feedback through publication networks, and manufactured consensus through coordinated academic conferences and publications. The program created lasting intellectual frameworks that continue influencing academic discourse today. Academic institutions employ subtle career penalties for researchers who challenge official narratives, creating powerful incentives for conformity. Contemporary academic funding structures perpetuate similar dynamics, where research contradicting official positions faces systematic obstacles to publication and promotion.
Contemporary COVID-19 Consensus Manufacturing
Recent COVID-19 lab leak consensus suppression demonstrates modern algorithmic enhancement of traditional Delphi manipulation techniques. Social media algorithms amplified manufactured expert consensus while suppressing alternative hypotheses, creating false scientific agreement that influenced policy decisions.
This operation integrated traditional expert manipulation with algorithmic feedback loops, achieving manipulation scores of 3.33/4.0 while maintaining moderate detection difficulty. The operation demonstrates how digital platforms enable real-time consensus manipulation at unprecedented scale .
Analysis: Increasing Sophistication and Detection Difficulty
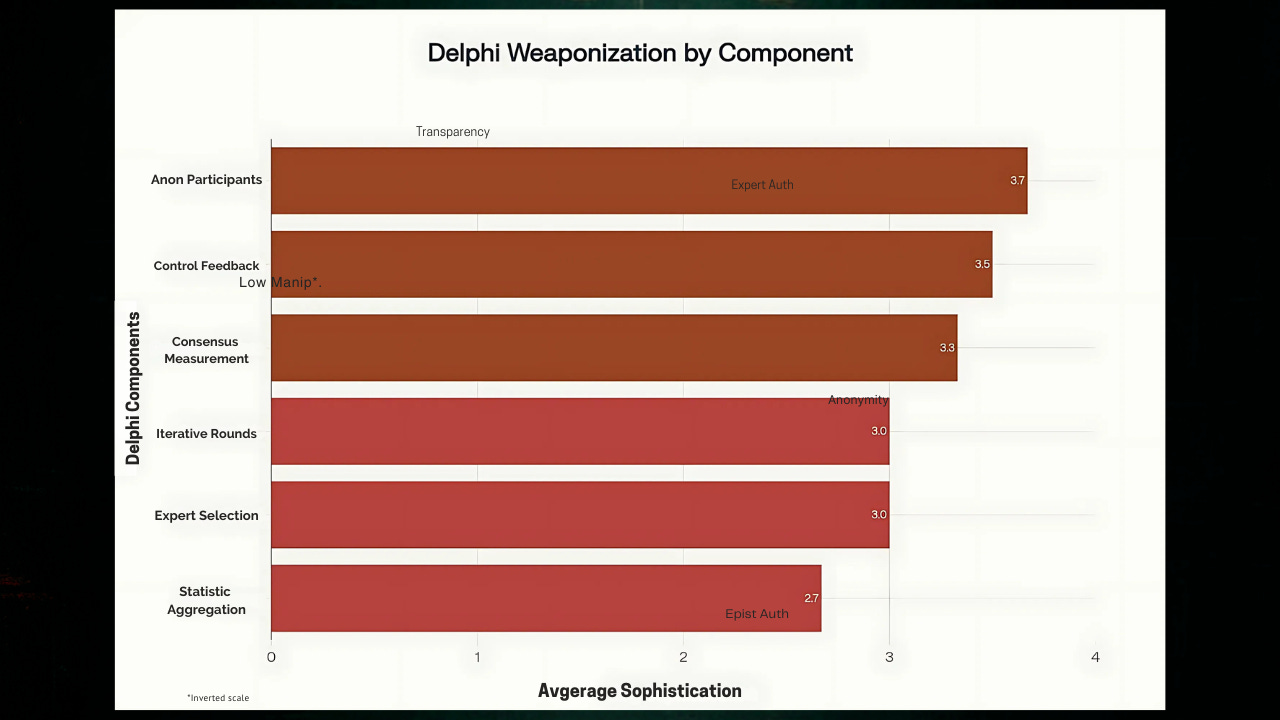
Research reveals systematic evolution in psychological operations sophistication, with contemporary examples achieving higher manipulation scores while becoming increasingly difficult to detect. Anonymous participation weaponization shows the highest average sophistication (3.67/4.0), followed by controlled feedback manipulation (3.5/4.0) and consensus measurement engineering (3.33/4.0).
Statistical aggregation remains the least sophisticated manipulation category (2.67/4.0), suggesting opportunities for defensive countermeasures focused on methodological transparency and verification. However, the overall trend toward increased sophistication indicates accelerating weaponization of consensus-building methodologies across multiple domains.
The integration of algorithmic amplification with traditional expert manipulation creates self-reinforcing systems that operate autonomously once established. These hybrid approaches achieve unprecedented scale while maintaining plausible deniability, representing a fundamental evolution in epistemological warfare capabilities.
The Systematic Subversion of Expert Consensus
A case can be made that, military psychological operations have transformed the Delphi method into a sophisticated weapon for manufacturing artificial consensus that serves strategic objectives rather than truth. These operations systematically exploit the method's core vulnerabilities—expert selection, feedback control, and consensus measurement—to create believable narratives that appear scientifically legitimate while advancing predetermined policy goals.
The increasing sophistication and detection difficulty of these techniques represents a fundamental threat to participatory insight production and informed public discourse. Understanding these mechanisms becomes essential for developing effective countermeasures that can preserve legitimate expertise while defending against systematic consensus manipulation.
Expert Authority Manipulation
Contemporary psychological warfare operations exploit the Delphi method's expert validation loops to construct artificial authority structures. Military mental health applications demonstrate how consensus-building techniques can be used to establish psychological frameworks that serve strategic objectives rather than genuine therapeutic needs. The method's anonymity features, originally designed to prevent expert dominance, can be inverted to obscure the true identities and qualifications of participants, enabling the construction of synthetic expert networks.
The intersection of military objectives and mental health care creates a unique environment where psychological frameworks are often developed through consensus-building techniques that prioritize operational effectiveness over individual therapeutic needs. These consensus-building methodologies, particularly the Delphi method, enable the systematic development of psychological frameworks that appear scientifically legitimate while primarily serving strategic military goals rather than optimal clinical care.
Military mental health applications consistently demonstrate a pattern where expert consensus processes establish treatment frameworks, diagnostic criteria, and intervention protocols that subtly subordinate genuine therapeutic outcomes to organizational imperatives like deployment readiness, force preservation, and combat effectiveness. The resulting frameworks create the appearance of scientific rigor while systematically prioritizing military objectives over individual recovery needs.
The Delphi Method in Military Mental Health: Manufacturing Strategic Consensus
Military Mental Health Provider Development
One of the most striking examples of consensus manipulation occurs in the development of military mental health provider frameworks through carefully controlled Delphi processes. A 2025 study utilized the Delphi method with 23 senior international military mental health experts to establish consensus on provider needs and development priorities. While appearing to address clinician wellbeing, the consensus-building process systematically prioritized organizational staffing requirements and mission readiness over provider sustainability.
The study defined the "most important needs" for military mental health providers as growth, respect, sense of belonging, and competence—all framed around maintaining organizational functionality rather than addressing the profound moral distress and secondary trauma experienced by providers in combat environments. This demonstrates how the Delphi method enables systematic prioritization of organizational needs while creating the appearance of addressing provider wellbeing.
Combat Operational Stress Control (COSC) Development
The development of Combat Operational Stress Control doctrine through expert consensus panels represents another clear example of strategic prioritization over therapeutic effectiveness. Despite over a century of development and refinement, systematic review evidence reveals that COSC frameworks have little to no effect on preventing PTSD or improving key mental health outcomes for military personnel.
The consensus-building process behind COSC focused on maximizing "unit combat effectiveness and individual personnel performance" rather than optimizing recovery outcomes. Expert panels systematically established stress control doctrine and metrics centered on rapid return-to-duty rates rather than comprehensive treatment protocols. This consensus-manufacturing approach enabled the military to create a framework that appears therapeutic while primarily serving force preservation objectives.
Strategic Frameworks Emerging from Manufactured Consensus:
Operational Stress Control and Readiness (OSCAR) Program
The Marine Corps' Operational Stress Control and Readiness program demonstrates how consensus methodology can create frameworks that maintain the appearance of therapeutic intent while serving primarily strategic objectives. Though OSCAR was developed through extensive expert consultation and consensus-building, evaluation research concluded that "this evaluation did not find evidence that OSCAR affected the key mental health outcomes it was designed to address".
Despite this lack of therapeutic effectiveness, OSCAR was deemed valuable by Marines as a "tool for enhancing combat and operational stress response and recovery efforts" —highlighting how consensus-built frameworks can serve strategic objectives while failing to address therapeutic needs. The program prioritized force readiness and retention over demonstrated improvement in mental health outcomes.
Military Fitness for Duty Evaluations
Consensus-building techniques have systematically shaped military fitness-for-duty evaluation frameworks to prioritize deployment readiness determination over individual mental health care. Expert panels establish psychological evaluation criteria consensus that focuses on "screening for psychological risk rather than pathology" —a subtle but critical shift that prioritizes mission capabilities over comprehensive treatment.
These frameworks systematically define "fitness" in terms that serve operational needs rather than therapeutic ones, creating a tension between risk screening and individual care. (We see a similar trend in education with OBE). The consensus process enables the development of standardized deployability criteria that appear scientifically legitimate while primarily serving force preservation objectives.
Moral Injury: Redefining Psychological Harm to Serve Institutional Needs
Individualizing Collective Responsibility
The development of moral injury frameworks through consensus techniques represents a particularly concerning example of psychological frameworks serving strategic objectives. Expert consensus has systematically shaped moral injury definitions to locate responsibility within the individual service member rather than acknowledging institutional responsibility for placing personnel in morally compromising situations.
This consensus-built framework serves to transfer the psychological burden of operational actions from the institution to the individual, creating a convenient framework for managing the aftermath of morally questionable operations. As one analysis notes, the military's definition of "spiritual fitness" in relation to moral injury "serves to locate moral responsibility for harmful acts performed during war within the individual service member, obscuring the role that military leadership and the military as an institution play". Another example of convenient placeing the onus on the individual to serve the collective, is the UN’s Inner Development Goals.
Creating Measurement Tools Through Consensus
The use of Delphi-style consensus techniques to develop moral injury measurement instruments further demonstrates this strategic redefinition of psychological harm. These consensus processes have created standardized moral injury assessment tools that identify symptoms in ways that place responsibility primarily on the individual's moral framework rather than on institutional decisions.
By controlling the expert selection, feedback processes, and consensus criteria, military organizations have inadvertently or otherwise, shaped moral injury conceptualization to serve institutional needs while appearing to address a genuine psychological concern. This consensus-manufactured framework enables the military to acknowledge psychological harm while avoiding institutional accountability .
Comprehensive Soldier Fitness: Consensus-Built Performance Enhancement
Resilience Over Recovery
The Comprehensive Soldier Fitness program demonstrates how expert committee consensus can develop frameworks that prioritize performance optimization over genuine wellness. This widely implemented program was developed through extensive expert consultation focused on building "resilience" defined primarily in terms of continued operational effectiveness rather than authentic psychological recovery.
The consensus-building process systematically shaped program goals around force preservation and combat readiness rather than addressing root causes of psychological distress. By defining resilience in operational terms, the consensus process created a framework that appears therapeutic while primarily serving the strategic goal of maintaining deployment capability.
Manufactured Consensus in Conflict Zones
Psychological warfare applications utilize modified Delphi techniques to manufacture consensus around strategic narratives. The Kayhan newspaper's psychological warfare campaign against Israel exemplifies how structured consensus-building can be weaponized, employing techniques such as selective information arrangement and false authority claims. These operations demonstrate the method's effectiveness in creating perceived expert agreement on contested political issues.
Cognitive Influence Operations
The integration of Delphi-derived techniques with modern psychological operations creates sophisticated cognitive influence campaigns. Artificial intelligence enhances these operations by automating expert credibility scoring and optimizing consensus formation algorithms, enabling large-scale manipulation of public opinion through apparently legitimate expert consultation processes.
Dialectical Warfare: Controlling Opposition
Perhaps the most sophisticated application of Delphi-derived techniques occurs in dialectical warfare, where the goal is not just to promote a specific viewpoint but to control the entire spectrum of permissible debate. By manufacturing both thesis and antithesis, operators can predetermine the eventual synthesis.
This approach creates controlled opposition—seemingly contradictory viewpoints that actually operate within carefully defined boundaries, creating the illusion of open debate while ensuring all permitted positions serve the same underlying objectives. Finnish information warfare training demonstrates exactly this approach, with teams competing for information space dominance using various manipulation techniques. This approach subverts genuine discursive reasoning by predetermining synthesis outcomes through expert network manipulation.
The result is a dialectical process that appears organic but operates as a closed system, with all permitted viewpoints ultimately reinforcing rather than challenging power structures. This weaponization of dialectics transforms unrestricted discourse into a simulation of debate that masks the absence of true alternatives. This was an interesting study— Dialectics of Complexity: A Five-Country Examination of Lived Experiences on Social Media.
to learn more about dialectics have a sneak peak at my upcoming book:
Hegel’s Dialectic, a Gnostic Jacob’s Ladder & the Machinery of Control:
Below is a sneak peak of a rough draft of my upcoming book! It’s still very much in development but I wanted to honor those supporting my work with a preview. I welcome, comments, suggestions and questions to help me improve the readers’ experience and understanding. Please forgive the potential typos, grammatical and spelling errors I may have overlooked, as this is a rough draft that will be edited and reformatted. I need to step away for a bit before I can do that competently. Thank you for supporting my work!
Political Consensus Engineering
Contemporary political warfare employs sophisticated consensus engineering techniques that build upon Delphi methodologies. Nicolás Maduro's social media operations in Venezuela demonstrate how information manipulation around contested knowledge claims can undermine democratic processes. Chinese "consensus elections" exemplify systematic political manipulation that maintains legitimacy while eliminating genuine competition.
Algorithmic Cybernetic Feedback Loops
Cybernetics is the transdisciplinary study of communication and control systems, both in living organisms and machines, focusing on how information is processed and used for regulation and feedback. It explores the principles of feedback, control, and communication, which are applicable across various fields like engineering, biology, and social systems. Cybernetics also encompasses the concept of the "cyborg," an organism with both natural and artificial systems, and is closely related to fields like artificial intelligence and robotics.
Algorithmic cybernetic feedback loops are self-regulating systems that use algorithms to process data, make decisions, and adjust actions based on feedback. These loops consist of three main components: a sensor to collect data, a processor to analyze and decide, and an actuator to implement changes. The system continuously monitors its output, compares it to a desired goal, and corrects deviations, creating a dynamic cycle. For example, a recommendation algorithm adjusts content suggestions based on user interactions, optimizing engagement. Such loops are foundational in automation, AI, and adaptive technologies, enabling systems to learn and improve over time.
Automated Consensus Formation
The integration of artificial intelligence with Delphi-inspired techniques creates autonomous consensus formation systems that operate through cybernetic feedback loops. These systems utilize machine learning algorithms to optimize expert selection, manipulate feedback processes, and generate synthetic evidence to support predetermined conclusions. The automation of consensus-building removes human oversight while maintaining the appearance of legitimate expert consultation.
Reinforcing Spiral Effects
Algorithmic cybernetic feedback loops create reinforcing spiral effects that amplify manipulated consensus outcomes. Media selectivity and effects processes generate mutually reinforcing patterns that consolidate artificial agreement while suppressing dissenting perspectives. These feedback mechanisms operate as positive loops in cybernetic systems, continuously strengthening manipulated consensus through algorithmic reinforcement.
Digital Fascism and Control Systems
The convergence of Delphi-derived techniques with algorithmic control systems enables what researchers term "digital fascism"—the reproduction of authoritarian ideologies through technological platforms. Social media algorithms exploit consensus-building principles to exacerbate social polarization while maintaining constant surveillance. These systems operate without requiring traditional leadership structures, instead using algorithmic feedback loops to maintain control.
The Digital Acceleration: Algorithmic Feedback Loops
Nato’s Cognitive Warfare document from 2021 explains how “hyper-personalized targeting integrating and exploiting neuroscience, bio-technology, information and cognitive tech-niques (NBIC), mainly using social media and digital networks for neuro-profiling and targeting individuals”… place “individuals are at the centre of all military operations and strategic-political decision-making.”
The fusion of Delphi’s wisdom with modern tech has birthed a power surpassing its founders’ wildest dreams. Today's algorithmic systems implement the method's core features at massive scale through automated systems that operate continuously and invisibly.
Social media algorithms create personalized feedback loops that mimic the controlled feedback mechanism of the original Delphi method. These systems selectively expose users to information that reinforces existing beliefs while creating the perception that those beliefs represent consensus. The resulting filter bubbles function as automated Delphi panels, continuously reinforcing manufactured consensus through algorithmic curation.
The Cybernetic Enhancement
What makes these systems truly dangerous is their cybernetic nature—they create self-reinforcing feedback loops that continuously shape both individual and collective behavior. Every interaction with these systems generates data that further refines the algorithm's ability to influence future behavior, creating an ever-tightening spiral of control.
Research demonstrates how these algorithmic feedback loops create reinforcing patterns that consolidate artificial agreement while suppressing dissenting perspectives. These digital systems operate as positive loops in cybernetic terms, continuously strengthening manipulated consensus through automated reinforcement.
The result is what researchers term "digital fascism"—the reproduction of authoritarian control mechanisms through technological platforms that maintain continuous surveillance. These systems operate without requiring traditional leadership structures, instead using algorithmic feedback loops to maintain control through the mechanics of the Delphi method at unprecedented scale.
Transformation into Epistemological Warfare
The transition from legitimate consensus-building to epistemological warfare occurred through several key adaptations. Modified Delphi applications began incorporating political objectives, reducing anonymity and expert authenticity while increasing manipulation potential. This evolution paralleled broader developments in information warfare, where cybernetic epistemology emerged as a framework for understanding complex social systems as controllable feedback mechanisms.

The weaponization process involved transforming the method's core components—expert selection, feedback control, consensus metrics, authority validation, and information dissemination—into interconnected manipulation systems. These components demonstrate high correlation coefficients, indicating their effectiveness as integrated warfare tools rather than independent mechanisms.
The Epistemological Battlefield: James Ferrier and the Origin of "Epistemology"
To fully understand how the Delphi method enables epistemological warfare, we must first examine the origin of epistemology itself—a term coined by Scottish philosopher James Frederick Ferrier in 1854. Ferrier's creation of this term represents a pivotal moment in the history of Western thought, one that laid the groundwork for our current epistemological crisis.
In his work "Institutes of Metaphysic," Ferrier introduced "epistemology" as "the theory of knowing," establishing a new domain of philosophical inquiry focused on the nature and validation of knowledge itself. While presented as a neutral philosophical contribution, this move effectively created a new battleground for controlling what counts as legitimate knowledge.
The Third Force: Western Occultism in Academic Disguise
What's rarely discussed in academic circles is Ferrier's connection to what would later be termed the "Third Force"— a humanistic psychological movement, repackaging Western occult traditions for scholarly appeal, veiled in the language of reason and science. This Third Force would later manifest most visibly in humanistic psychology, positioned as an alternative to behaviorism and psychoanalysis. While this discussion warrants its own comprehensive exploration, for the purposes of the current essay it’s important to note Ferrier’s emphasis on mind-dependent reality and self-knowledge parallels mystical tradition.
The Third Force operated by integrating esoteric concepts into academic discourse while stripping away their explicit spiritual and occult origins. This movement created a bridge between ancient mystical traditions and modern scientific discourse, enabling the continuation of hierarchical knowledge systems under the appearance of rational inquiry.
Ferrier's work established epistemology as a formal domain that could arbitrate what qualified as legitimate knowledge. By creating this specialized field, he effectively established a gatekeeping mechanism that could exclude certain forms of knowing while privileging others—all under the appearance of neutral philosophical inquiry.
From Theory of Knowing to Mechanism of Control
The establishment of epistemology as a formal discipline had profound implications for how knowledge would be controlled in Western societies. By creating specialized terminology and methodologies for evaluating knowledge claims, Ferrier and his successors established systems that could effectively filter information based on whether it conformed to established power structures.
This process created hierarchies of knowledge where institutional expertise gained primacy over direct experience or traditional wisdom. The seemingly neutral philosophical inquiry of epistemology thus became a powerful tool for determining whose knowledge would be taken seriously and whose would be dismissed—a function that mirrors the expert selection mechanism of the Delphi method.
The connections between Ferrier's epistemology and the mechanics of the Delphi method are not coincidental. Both establish systems for determining what counts as legitimate knowledge, both rely on specialized experts to validate claims, and both create feedback mechanisms that reinforce established authority while marginalizing alternative perspectives.
Reactionary Epistemology: The Bootstrap Response
As institutional epistemology became increasingly captured by power structures, a counter-movement emerged that we now recognize as "reactionary epistemology". This approach rejects institutional expertise in favor of individual research and direct experience—a position that initially appears liberating but creates its own vulnerabilities to manipulation.
The Bootstrap Narrative
At the heart of reactionary epistemology lies what researchers term "bootstraps epistemology"—a narrative that encourages individuals to reject institutional knowledge in favor of personal research and intellectual combat with opponents. Just as the political "bootstraps" narrative argues individuals must reject "handouts" and improve through personal effort, bootstraps epistemology urges rejection of established expertise in favor of self-directed knowledge-seeking.
The term "reactionary epistemology" is derived from the work of Dr. Cindy Ma, a lecturer in Race and Media at the University of Leeds. It emerged from her research on reactionary YouTube channels and their audiences, as detailed in her 2023 paper, "Thinking for Themselves: Bootstraps Discourse and the Imagined Epistemology of Reactionary YouTube Audiences," published in Political Communication. While Ma primarily introduces "bootstraps epistemology," the term "reactionary epistemology" is implied or used interchangeably in discussions of her work to describe the broader epistemological framework of reactionary groups. Her research draws on over two years of fieldwork, including qualitative analysis of YouTube content and interviews with 18 fans of reactionary channels.
Ma coined "bootstraps epistemology" to describe how reactionary influencers and their audiences claim to arrive at political beliefs through a self-reliant, individualistic process of "personal research and rational deliberation." The term draws on the metaphor of "pulling oneself up by one’s bootstraps," emphasizing rugged individualism and distrust of institutional knowledge. This approach has gained tremendous currency as trust in mainstream institutions has collapsed, with alternative media sources providing seemingly independent information that challenges official narratives. The individual becomes their own arbiter of truth, assembling personally convincing evidence rather than deferring to institutional expertise.
Research into reactionary YouTube channels and their audiences reveals how this epistemological approach appeals to viewers seeking alternatives to mainstream narratives. Interviews with viewers demonstrate how they conceptualize their political formation as a highly personal journey of research and rational deliberation, rather than adoption of established perspectives. While I encourage independent research and analysis, this purported liberation from institutional manipulation creates new vulnerabilities to sophisticated alternative manipulation campaigns designed to exploit confirmation bias and the illusion of independent research.
The Paradoxical Vulnerability
The tragic irony of bootstraps epistemology is that while it appears to liberate individuals from manipulated consensus, it creates new vulnerabilities to sophisticated manipulation. By rejecting institutional gatekeeping, individuals become susceptible to carefully constructed alternative narratives that exploit confirmation bias and the illusion of independent research.
This creates perfect conditions for advanced applications of Delphi-derived techniques, where seemingly diverse sources can be coordinated to create the appearance of independent convergence on predetermined conclusions. The individual researcher, lacking institutional resources to verify claims, becomes vulnerable to sophisticated disinformation campaigns designed to exploit their desire for independent verification.
Research demonstrates that anti-intellectual and anti-expertise attitudes paradoxically enhance rather than diminish susceptibility to manipulation. When individuals reject institutional knowledge systems entirely, they lose access to collective verification mechanisms that, despite their flaws, provide some protection against targeted manipulation.
Epistemological Warfare Mechanisms
Authority Construction and Validation
Epistemological warfare employs Delphi-derived mechanisms to construct and validate artificial authority structures that shape knowledge production. The concept of "bootstraps epistemology" demonstrates how reactionary movements exploit individual research narratives to undermine institutional knowledge authorities. This process involves creating alternative expert networks that appear legitimate while serving ideological objectives rather than truth-seeking goals.
Consensus Manufacturing Systems
Modern epistemological warfare operations utilize algorithmic consensus manufacturing that builds upon traditional Delphi foundations. These systems create artificial agreement through coordinated manipulation techniques, including targeted amplification and manufactured consensus, as evidenced in social media operations. The platforming of information creates opacity that generates manipulative effects on consensus-building dynamics.
Information Ecosystem Control
Epistemological warfare systems integrate Delphi-inspired techniques with broader information control mechanisms. Digital authoritarianism leverages these methods to create surveillance and manipulation systems that operate without requiring centralized control, instead using algorithmic feedback loops to maintain epistemic dominance. The method's original emphasis on statistical representation becomes a tool for creating false legitimacy around manipulated consensus outcomes.
Fostering Reactionary Epistemology
Individual Research Narratives
Reactionary epistemology emerges through the systematic exploitation of individual research narratives that mimic traditional Delphi consultation processes. "Bootstraps epistemology" encourages people to reject institutional expertise in favor of personal research and intellectual combat with opponents. This approach undermines collective knowledge production while maintaining the appearance of rigorous individual investigation. While I typically encourage independent analysis and insight, those who are conditioned to distrust established pipelines might be vulnerable targets of 5th generation warfare.
Anti-Expertise Sentiment Cultivation
The weaponization of Delphi techniques contributes to cultivating anti-expertise sentiment that serves reactionary political objectives. Research demonstrates that anti-intellectual, anti-science, and anti-expertise attitudes create paradoxical relationships with expert influence, where mistrust enhances rather than diminishes susceptibility to manipulation. This dynamic enables sophisticated manipulation through channels that exibit anti-establishment messaging.
Contemporary reactionary epistemology integrates algorithmic bias systems that automate the production of manipulated consensus. These systems create self-reinforcing cycles where biased algorithms generate evidence that supports predetermined reactionary conclusions.
Contemporary Implications and Systemic Analysis
Cybernetic Control Architecture
The evolution of Delphi-derived techniques into cybernetic control systems represents a fundamental transformation in how consensus manipulation operates. Cybernetic epistemology provides the theoretical framework for understanding knowledge as practice embedded within organism-environment feedback loops rather than independent representation. This perspective enables the systematic engineering of knowledge production through controlled feedback mechanisms.
Network Effects and Scaling
Modern consensus manipulation systems achieve unprecedented scale through network effects that amplify traditional Delphi limitations. The digital ecosystem enables manipulation techniques ranging from targeted amplification to manufactured consensus, creating coordinated activity that can influence offline actions and organized violence. These network effects transform localized expert manipulation into society-wide epistemological control systems.
Detection and Resistance Challenges
The sophistication of contemporary epistemological warfare creates significant challenges for detection and resistance. Critical thinking and analytical reasoning, while important, prove insufficient against systematic manipulation that exploits cognitive biases and social dynamics. The gap between understanding manipulation techniques and developing effective countermeasures reflects the advanced nature of cybernetic feedback systems that operate below conscious awareness thresholds.
The Strategic Objective: Epistemological Collapse
The ultimate objective of these operations transcends traditional political goals—their purpose is to create epistemological collapse, where shared reality itself fragments into irreconcilable tribal narratives. This collapse serves strategic interests by paralyzing America's ability to recognize and respond to threats while communities fight over fundamental reality claims.
What makes these operations particularly effective is their exploitation of legitimate institutional failures. Real breaches of public trust provide fertile ground for campaigns that aim to completely delegitimize remaining functional systems. By amplifying genuine failures and mixing them with manufactured narratives, these operations create plausible ecosystems of alternative explanation that erode confidence in all institutional knowledge.
The strategic advantage of this approach is that it requires no centralized control. Once the initial conditions are established, algorithmic feedback loops and social dynamics create self-sustaining cycles of reality fragmentation. The weaponization of the Delphi method's core mechanics—expert selection, controlled feedback, and manufactured consensus—creates systems that continue operating autonomously once deployed.
The Synthesis: Cybernetic Epistemology and the Future of Knowledge
As we confront these challenges, a new understanding of knowledge itself becomes necessary—one that recognizes the cybernetic nature of modern information environments. Cybernetic epistemology offers a framework for understanding knowledge not as static representation but as dynamic patterns of organism-environment interaction operating through feedback loops.
This perspective enables us to recognize the fundamental transformation in how knowledge is produced, validated, and disseminated in contemporary society. What began with Ferrier's formalization of epistemology and evolved through the Delphi method has now culminated in algorithmic systems that shape knowledge through continuous feedback cycles.
Reclaiming Cognitive Liberty & Sovereignty
The path forward requires neither blind acceptance of institutional expertise nor complete rejection of collective knowledge systems. Instead, we must develop new approaches that preserve the benefits of collective verification while protecting against the vulnerabilities of both institutional capture and individualistic manipulation.
This begins with recognition of the mechanisms being deployed against us. By understanding how the Delphi method's principles operate within modern information environments, we can identify manipulation techniques that would otherwise remain invisible. This recognition creates the possibility of conscious resistance to otherwise unconscious influence.
The most effective counter to these operations is neither blind trust nor complete rejection, but rather the development of resilient knowledge communities that combine institutional resources with grassroots verification. These communities can provide the collective cognitive infrastructure necessary to evaluate complex claims while remaining responsive to direct experience and new evidence.
Modern Cybernetic Warfare Mechanisms
Algorithmic Feedback Loops and Digital Amplification
Contemporary epistemological warfare employs sophisticated cybernetic feedback loops that automate and amplify the core mechanisms of Delphi and T-group manipulation . These systems create self-reinforcing cycles where algorithmic responses to user behavior generate increasingly sophisticated targeting and manipulation capabilities . Research demonstrates how financial and criminal risk assessment algorithms create perpetual bias cycles that systematically disadvantage marginalized populations through feedback loop mechanisms.
The cybernetic nature of these systems enables autonomous operation without requiring direct human oversight, creating what researchers term "digital fascism" through technological reproduction of authoritarian control mechanisms . These feedback loops facilitate real-time adaptation to user responses, continuously refining manipulation techniques based on behavioral data collection and analysis .
Platform-Mediated Targeting Systems
Modern social media platforms implement targeting mechanisms that directly correlate with original Delphi and T-group manipulation techniques . Content moderation systems demonstrate systematic bias against marginalized users, employing algorithmic discrimination that mirrors the expert selection and controlled feedback mechanisms of historical consensus manipulation methods. Research reveals that AI-powered content moderation exhibits pronounced demographic bias, with female-specific content facing stricter regulation compared to male-specific content.
The matrix of targeting mechanisms reveals how platform-based suppression techniques systematically implement core principles of historical manipulation methods through shadow banning, demonetization, search suppression, and recommendation bias . These digital tools create the same epistemological isolation effects achieved through traditional group manipulation while operating at unprecedented scale and sophistication.
Targeting Independent and Dissident Voices
Bootstraps Epistemology Exploitation
As mentioned above, research into reactionary YouTube audiences reveals how this epistemological approach appeals to viewers seeking alternatives to mainstream narratives, with participants conceptualizing their political formation as highly personal journeys of research and rational deliberation. However, this apparent liberation from institutional manipulation creates new vulnerabilities to sophisticated alternative manipulation campaigns designed to exploit confirmation bias and the illusion of independent research.
Platform-Specific Targeting Strategies
Analysis of content moderation practices reveals systematic bias against marginalized and independent voices across major social media platforms . The visibility of moderation practices varies significantly between platforms, with text-based platforms making moderation invisible to users while live streaming platforms expose these practices through real-time chat interactions and "unban appeal" streams. This differential visibility creates strategic opportunities for manipulation while obscuring accountability mechanisms .
Platform market structure analysis demonstrates that decentralized online environments may actually facilitate authoritarian control by creating strategic incentives for compliance with censorship requests. Smaller platforms delay compliance to attract users fleeing from competitors who quickly comply with censorship demands, but this creates predictable patterns that can be exploited for systematic suppression.
Algorithmic Manipulation and Reactionary Epistemology
Cancel Culture as Epistemological Warfare
Contemporary cancel culture represents an unprecedented form of intellectual and political totalitarianism that reactivates practices similar to those employed in Soviet and Chinese cultural revolution contexts. This phenomenon demonstrates how epistemological warfare can be deployed within academic and cultural institutions to suppress dissenting voices while maintaining the appearance of moral righteousness. The systematic nature of these attacks reveals coordinated manipulation that transcends individual incidents to constitute systematic epistemological suppression.
AI-Driven Content Control
Modern artificial intelligence systems demonstrate systematic bias in content moderation that affects political discourse and independent media. Large language models exhibit bias during content moderation across different demographics and minority communities, with particular impact on independent content creators who challenge mainstream narratives. The lack of transparency in AI decision-making processes creates opportunities for pervasive manipulation while obscuring accountability for biased outcomes.
Research reveals that generative AI content moderation often results in over-censorship that disproportionately affects independent voices. These systems often create systematic suppression of alternative viewpoints.
Contemporary Landscape in the United States
Deplatforming and “Digital Sovereignty”
“Digital Sovereignty” is an oxymoron, but alas well save that conversation for another article, since the term has become a pervasive “buzzword”. The systematic de-platforming of independent media represents a direct assault on sovereignty in the digital realm, with local and regional social platforms serving as the primary defense against data colonialism, disinformation, and algorithmic manipulation. These alternative platforms help combat those challenges, however their effectiveness remains limited by the overwhelming dominance of major platform ecosystems.
Systematic Surveillance and Control
Research into mean field social control demonstrates how algorithmic systems enable decentralized manipulation strategies that operate without requiring traditional centralized authority structures. These systems employ integral reinforcement learning techniques to develop data-driven methods for population control that adapt to resistance and evolve countermeasures autonomously . The robustness of these algorithms ensures convergence toward desired outcomes even in the presence of disturbances or opposition.

The Cybernetic Epistemological Battlefield
The evolution from traditional Delphi methods and T-groups to contemporary algorithmic manipulation represents a fundamental transformation in the nature of epistemological warfare. Modern cybernetic feedback loops enable autonomous manipulation systems that continuously adapt to resistance while maintaining the appearance of neutral technological operation. The systematic targeting of independent and dissident voices through these mechanisms constitutes a direct assault on democratic discourse and cognitive sovereignty.
Understanding these connections becomes essential for developing effective countermeasures against sophisticated manipulation campaigns that exploit both institutional vulnerabilities and individual epistemological weaknesses. The convergence of historical consensus manipulation techniques with modern algorithmic capabilities creates an urgent need for new approaches to protecting intellectual freedom and authentic democratic participation in an increasingly manipulated information environment.
The battle for epistemological sovereignty requires recognition that current targeting systems represent the sophisticated evolution of manipulation techniques that have been refined over decades of research and development. Only through understanding these historical connections and contemporary applications can effective resistance be developed against the systematic suppression of independent thought in American society.
Conclusion: From Group Manipulation to Algorithmic Consensus Manufacturing
The Unbroken Chain of Epistemological Control
The weaponization of the Delphi method represents the culmination of a seventy-year evolution in consensus manipulation that began with Kurt Lewin's sensitivity training experiments during World War II. What emerges from this historical analysis is not a series of unrelated developments, but rather an unbroken chain of epistemological control that has transformed from intimate group manipulation into the vast algorithmic systems that now aim to shape global consciousness towards Teilhard de Chardin’s vision of the Noosphere.
Sensitivity training provided the foundational understanding of how psychological pressure, controlled feedback, and manufactured consensus could override individual critical thinking. Kurt Lewin's work at MIT and the subsequent development of T-groups at the National Training Laboratory demonstrated that human beings could be systematically conditioned to conform to predetermined outcomes through carefully orchestrated group dynamics. The Tavistock Institute's refinement of these techniques revealed their potential for large-scale social engineering, establishing the theoretical framework that would later be operationalized through more sophisticated methods.
The RAND Corporation's development of the Delphi method in the 1950s represented the crucial bridge between intimate group manipulation and systematic consensus manufacturing. By formalizing the core mechanisms discovered in sensitivity training—expert selection, controlled feedback, iterative refinement, and statistical validation—the Delphi method created a scalable methodology for manufacturing artificial agreement while maintaining the appearance of scientific objectivity. What began as psychological experiments on small groups evolved into a systematic approach for controlling knowledge production across entire expert networks.
The Cybernetic Revolution: From Human Facilitators to Algorithmic Orchestration
The true transformation occurred with the integration of cybernetic principles and algorithmic automation. Modern social media platforms have become vast, automated Delphi panels operating at unprecedented scale. Every user interaction generates data that feeds back into recommendation algorithms, creating self-reinforcing cycles of consensus manipulation that operate below the threshold of conscious awareness.
These algorithmic feedback loops represent the technological apotheosis of sensitivity training principles. Where T-groups required skilled human facilitators to guide participants toward predetermined outcomes, today's systems employ artificial intelligence to automatically identify psychological vulnerabilities, customize manipulative content, and orchestrate consensus formation across millions of users simultaneously. The controlled feedback mechanism that characterized both sensitivity training and the Delphi method has been amplified through machine learning algorithms that continuously refine their manipulation techniques based on user response patterns.
The cybernetic nature of these systems creates what researchers term "digital fascism"—the reproduction of authoritarian control mechanisms through technological platforms that operate without requiring traditional centralized leadership. These systems exploit the same psychological mechanisms discovered by Lewin and his colleagues: the human tendency toward conformity, the power of perceived expert consensus, and the effectiveness of incremental pressure in overcoming individual resistance.
Epistemological Warfare and the Manufacture of Reality
Contemporary epistemological warfare represents the strategic deployment of these evolved techniques to undermine the very foundations of shared reality. The goal is not merely to promote specific viewpoints, but to create what scholars term "epistemological collapse"—a condition where societies lose the ability to distinguish between truth and falsehood, rendering collective action impossible.
The sophistication of modern consensus manipulation far exceeds anything imagined by the original developers of sensitivity training or the Delphi method. Artificial intelligence systems now conduct real-time psychological profiling, deploy personalized manipulation campaigns, and coordinate across multiple platforms to create the illusion of organic consensus emergence. The anonymity and expert validation mechanisms that characterized the original Delphi method have been enhanced through algorithmic systems that can manufacture synthetic expert networks and artificial authority structures at will.
Research reveals that these operations have achieved unprecedented sophistication in their ability to target specific populations, exploit cognitive biases, and create self-reinforcing information ecosystems that insulate users from contradictory evidence. The controlled feedback loops that once required careful human orchestration now operate autonomously through algorithmic systems that continuously adapt their manipulation strategies based on user behavior.
The Existential Threat to Cognitive Sovereignty
What we face today is nothing less than an existential threat to cognitive sovereignty—the fundamental human capacity for independent thought and collective truth-seeking. The techniques pioneered in sensitivity training and systematized through the Delphi method have evolved into algorithmic systems capable of manipulating consciousness itself. These systems operate not merely as tools of persuasion, but as mechanisms for reshaping the cognitive infrastructure through which human beings understand reality.
The implications extend far beyond traditional concerns about propaganda or misinformation. Contemporary consensus manipulation systems can create what researchers term "synthetic realities"—artificially constructed information environments that become self-sustaining through cybernetic feedback loops. Users trapped within these systems experience not just exposure to false information, but systematic alteration of their capacity for critical evaluation and independent thought.
The targeting of independent and dissident voices reveals the strategic objectives of these operations. By systematically suppressing alternative perspectives and manufacturing artificial consensus around predetermined narratives, these systems work to eliminate the cognitive diversity necessary for healthy unrestricted discourse. The result is not merely political manipulation, but the systematic engineering of intellectual conformity on a civilizational scale.
The Imperative for Cognitive Liberation
The battle for cognitive liberty represents the defining struggle of our time. The techniques that began with sensitivity training and evolved through the Delphi method have reached a level of sophistication that threatens the fundamental prerequisites for human freedom— the capacity for independent thought, the ability to evaluate evidence critically, and the possibility of achieving genuine consensus through unrestricted discourse.
Understanding this progression becomes essential for developing effective resistance strategies. The same mechanisms that enable these systems to manipulate consciousness can be understood and countered by those committed to preserving cognitive liberty. Recognition of how consensus is manufactured rather than discovered, represents the first step toward reclaiming our cognitive sovereignty from systems designed to shape rather than serve human understanding.
The path forward requires neither blind trust in captured institutions nor retreat into vulnerable individualism, but rather the conscious construction of resilient knowledge communities that combine collective verification with protection against systematic manipulation. By understanding the historical development and technical mechanisms of consensus manufacturing, we can begin to develop the cognitive immune systems necessary to preserve authentic human agency in an age of algorithmic control.
The stakes could not be higher. The future of human consciousness itself hangs in the balance as we confront systems designed to manufacture the very reality we perceive. Only through understanding the full scope of this threat—from its origins in post-war psychological research through its contemporary manifestation in algorithmic consensus manufacturing—can we hope to preserve the cognitive freedom upon which all other freedoms ultimately depend.
The choice before us is clear: submit to manufactured consensus or reclaim our birthright as conscious, thinking beings capable of discovering truth through genuine dialogue and unbridled inquiry. The techniques that once manipulated small groups in laboratory settings now shape the consciousness of billions. Understanding their operation becomes not merely an academic exercise, but a fundamental requirement for preserving human agency in the 21st century.
Our cognitive sovereignty depends on our willingness to confront these mechanisms and consciously choose authentic knowledge over manufactured consensus. The future of human consciousness—and the possibility of genuine self- governance— hangs in a precarious balance.
Primary Sources and Foundational Documents
The Delphi Method Origins
Dalkey, Norman C., and Olaf Helmer. The Delphi Method: An Experimental Study of Group Opinion. RAND Corporation, 1962.
RAND Corporation Archive
RAND Corporation. Generating Evidence Using the Delphi Method (2023).
https://www.rand.org/pubs/commentary/2023/10/generating-evidence-using-the-delphi-method.html
Sensitivity Training and Group Dynamics
Lewin, Kurt. Group Dynamics: Research and Theory. Massachusetts Institute of Technology Research Center for Group Dynamics, 1946.
Internet Archive
MBA Knowledge Base. Sensitivity Training - Meaning, History, and Stages.
https://www.mbaknol.com/modern-management-concepts/sensitivity-training/
National Training Laboratory. Historical Documentation - Bethel, Maine Training Center.
What is Tavistock Institute Group Relations thinking? Tavistock Institute of Human Relations
Intelligence and Military Documents
CIA Documents
Burkett, Randy. An Alternative Framework for Agent Recruitment: From MICE to RASCALS. CIA Studies in Intelligence, Vol. 57, No. 1 (March 2013).
https://www.cia.gov/resources/csi/studies-in-intelligence/volume-57-no-1/an-alternative-framework-for-agent-recruitment-from-mice-to-rascls/
PDF Archive: https://cyberwar.nl/d/fromCIA.gov/Burkett-MICE%20to%20RASCALS.pdf
NATO Documents
du Cluzel, François. Cognitive Warfare. NATO Joint Warfare Centre, 2021.
VoltaireNet
Key Books and Monographs
Education and Social Engineering
Iserbyt, Charlotte Thomson. The Deliberate Dumbing Down of America: A Chronological Paper Trail. Conscience Press, 2000.
Internet Archive
Philosophy and Epistemology
Ferrier, James Frederick. Institutes of Metaphysic (1854).
Internet Encyclopedia of Philosophy
Chase, Stuart. The Proper Study of Mankind: An Inquiry into the Science of Human Relations (1948).
Internet Archive
Political Organizing and Influence
Alinsky, Saul. Rules for Radicals (1971).
Obsidian Publish Summary
Cialdini, Robert B. Influence: The Psychology of Persuasion.
Global Governance
King, Alexander and Schneider, Bertrand. The First Global Revolution. Club of Rome, 1991.
Internet Archive
Academic Papers and Research
Epistemology and Media Studies
Ma, Cindy. "Thinking for Themselves: Bootstraps Discourse and the Imagined Epistemology of Reactionary YouTube Audiences." Political Communication, 2023.
University of Leeds News
Delphi Method Research
Niederberger, Marlen, Stefan Köberich, et al. "Coming to consensus: the Delphi technique." European Journal of Cardiovascular Nursing, Volume 20, Issue 7, October 2021, Pages 692–695.
Oxford Academic
Fink-Hafner, Danica, et al. "Delphi Method: Strengths and Weaknesses." Metodološki zvezki, Vol. 16, No. 2, 2019, 1–19.
University of Ljubljana PDF
Dayé, Christian "How to train your oracle: The Delphi method and its turbulent youth in operations research and the policy sciences." Vol.48 No.6
Sage Journals, Social Studies of Science
Gordon, Theodore J. "THE REAL-TIME DELPHI METHOD."
The Millennium Project - Futures Research Methodology V3.0
Medical and Healthcare Applications
PubMed Central. "Expert Consensus Based Evidence Using the Delphi Method."
https://pubmed.ncbi.nlm.nih.gov/30509437/
PMC Articles. "Delphi methodology in healthcare research: How to decide its appropriateness." July 20, 2021.
https://pmc.ncbi.nlm.nih.gov/articles/PMC8299905/
Institutional and Organizational Sources
Tavistock Institute
Rees, John Rawlings. "The Shaping Of Psychiatry By War” 1945.
Biographical entry. Encyclopedia.com.
Trist, Eric. Autobiography, “Guilty of Enthusiasm”.
http://www.moderntimesworkplace.com/archives/ericbio/ericbio.html
European Union
European Commission Joint Research Centre. The Future of Customs in the EU 2040: A Foresight Study.
YouTube Intro
Research Institutions
Better Evaluation. "Delphi study methodology."
https://www.betterevaluation.org/methods-approaches/methods/delphi-study
Science.gov. "Modified Delphi Method: Topics by Science.gov."
https://www.science.gov/topicpages/m/modified+delphi+method.html
Historical and Reference Sources
General Reference
Wikipedia. "Delphi method."
https://en.wikipedia.org/wiki/Delphi_method
"Charlotte Thomson Iserbyt."
https://deliberatedumbingdown.com/ddd/
Technical Resources
“Generating Evidence Using the Delphi Method” https://www.rand.org/pubs/commentary/2023/10/generating-evidence-using-the-delphi-method.html
“RAND Methodological Guidance for Conducting and Critically Appraising Delphi Panels” https://www.rand.org/content/dam/rand/pubs/tools/TLA3000/TLA3082-1/RAND_TLA3082-1.pdf
“Setting the Record Straighter on Shadow Banning” https://arxiv.org/pdf/2012.05101
Additional Source Materials
Literary References
Pope, Alexander. "Essay on Man, Epistle II" (1733) - Referenced for the phrase "The proper study of mankind is man."
Poetry Foundation
Archive Sources
Internet Archive. Multiple historical documents and books referenced throughout.
Archive.org
*note- Graphs presented are estimated representations based on my research not precise statistical analyses.











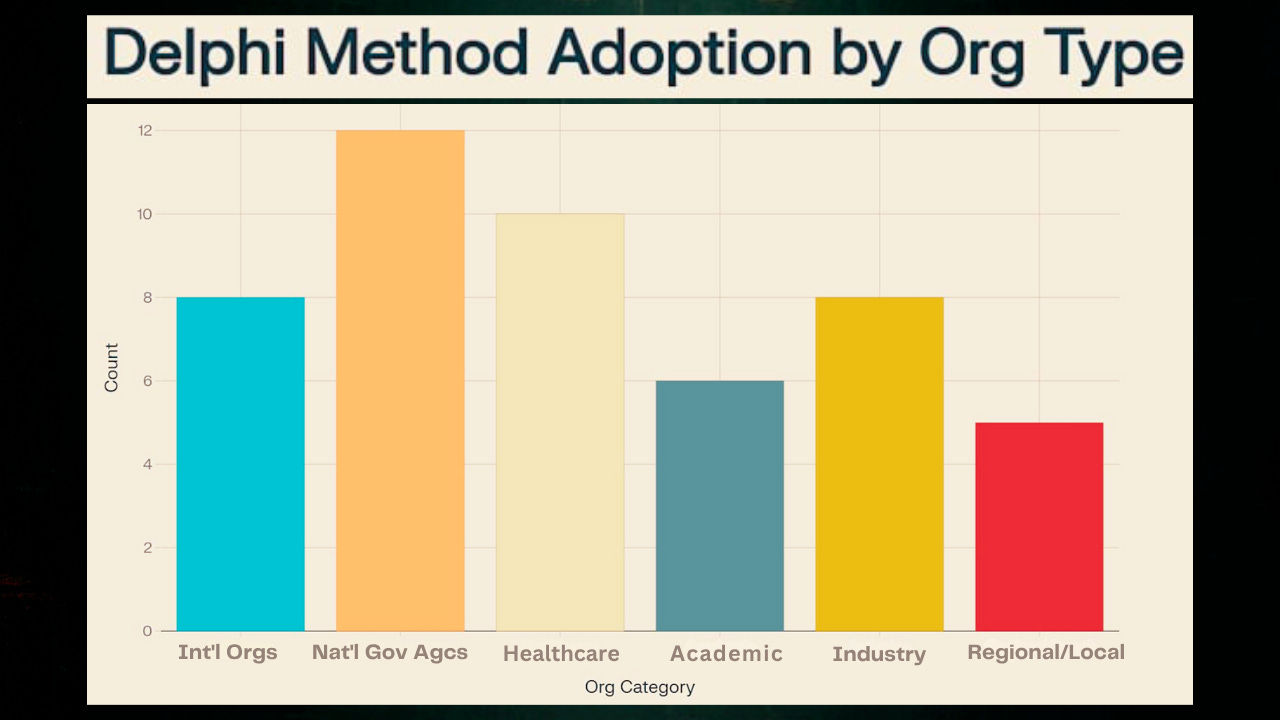






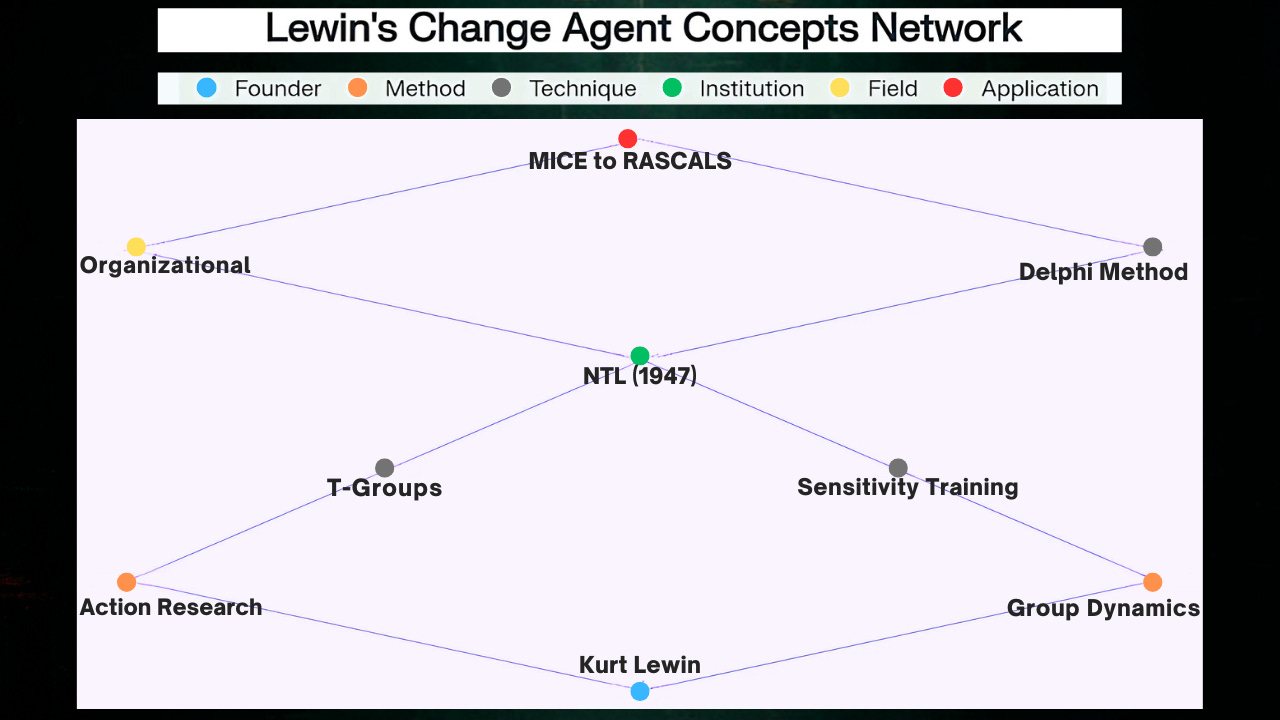

























I am very interested in printed form of your essay so that I can study it. I appreciate your work here.